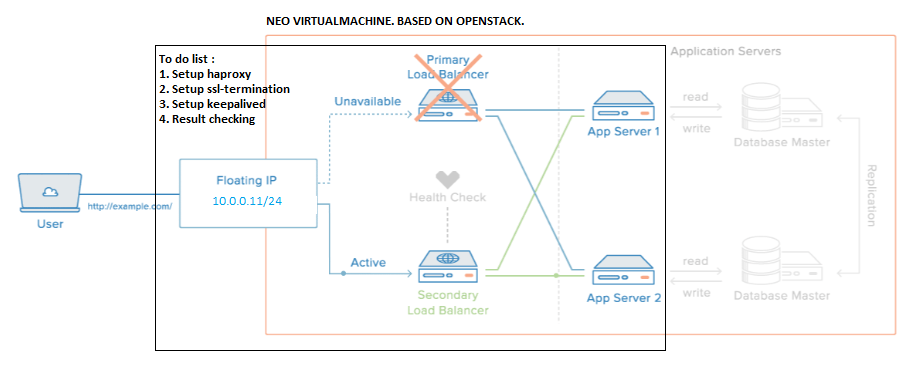
Logical Topology
Requirements
- IP protocol 112 (VRRP) must be supported in the network.
- If you use multicast, the network must support multicast request (use ip a | grep -i multicast).
- Already have ssl certificate components (.key .crt .ca) and bundling as pem for domain.
First thing to do
- Finish web and db connection setup.
- Synchronize web nodes data using lsync.
- Disabling all firewall services and selinux (/etc/selinux/config).
- Activate packet forwarding and non-binding setup on lb-nodes.
cat >> /etc/sysctl.conf net.ipv4.ip_nonlocal_bind=1 net.ipv4.ip_forward = 1 sysctl -p - Install haproxy and keepalived on lb-nodes.
Section 1 - Openstack configuration
- Grep port-id of instance :
nova interface-list [instance-name]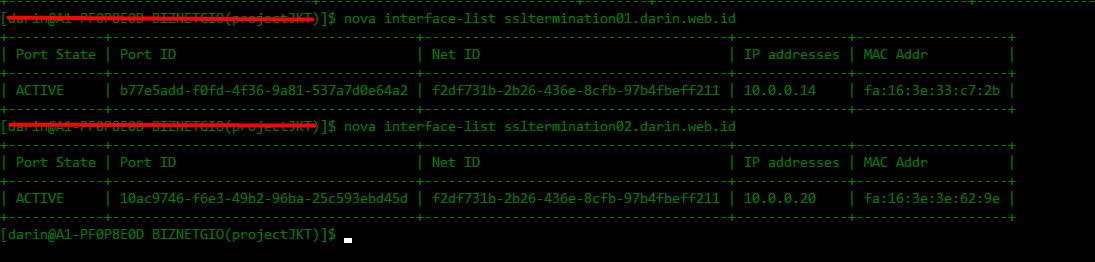
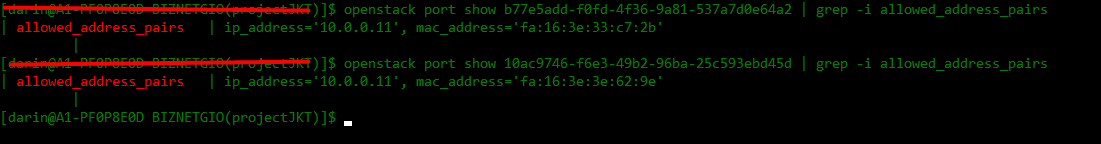
- View allowed address pair of that port-id :
openstack port show [port-id] | grep -i allowed_address_pairs - Add the virtual floating ip to each port :
neutron port-update [port-id] --allowed_address_pairs list=true type=dict ip_address=[dedicated-ip-address]neutron port-update 10ac9746-f6e3-49b2-96ba-25c593ebd45d --allowed_address_pairs list=true type=dict ip_address=10.0.0.11 neutron port-update b77e5add-f0fd-4f36-9a81-537a7d0e64a2 --allowed_address_pairs list=true type=dict ip_address=10.0.0.11 - View allowed address pair of updated port-id
Section 2 - HAproxy configuration LB01 - ssltermination01.darin.web.id
cp /etc/haproxy/haproxy.cfg haproxy.cfg.default
touch /var/log/haproxy.log
vim /etc/haproxy/haproxy.cfg
#enable this line
log 127.0.0.1 local2
vim /etc/rsyslog.conf
#uncomment this line
$ModLoad imudp
$UDPServerRun 514
cat >> /etc/rsyslog.d/haproxy.conf
local2.* /var/log/haproxy.log
service rsyslog restart
service rsyslog status
tail -f /var/log/haproxy.log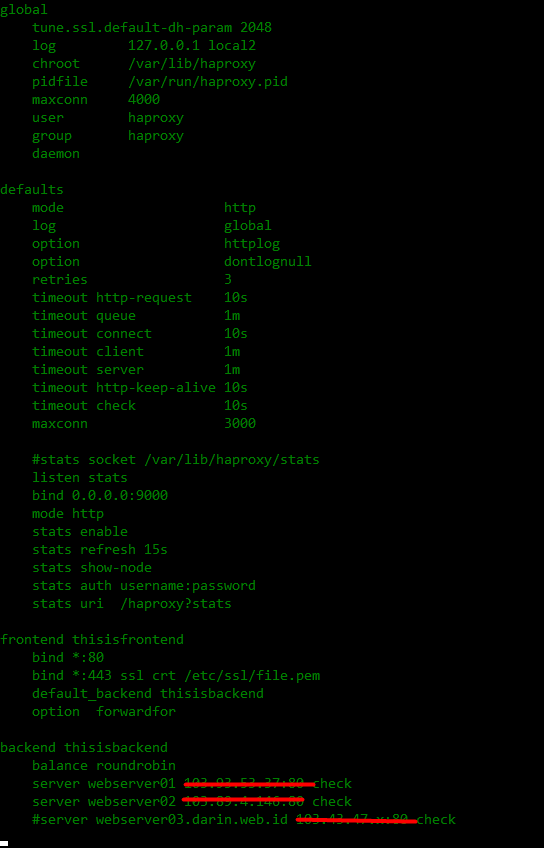
LB02 - ssltermination02.darin.web.id
cp /etc/haproxy/haproxy.cfg haproxy.cfg.default
touch /var/log/haproxy.log
vim /etc/haproxy/haproxy.cfg
#enable this line
log 127.0.0.1 local2
vim /etc/rsyslog.conf
#uncomment this line
$ModLoad imudp
$UDPServerRun 514
cat >> /etc/rsyslog.d/haproxy.conf
local2.* /var/log/haproxy.log
service rsyslog restart
service rsyslog status
tail -f /var/log/haproxy.log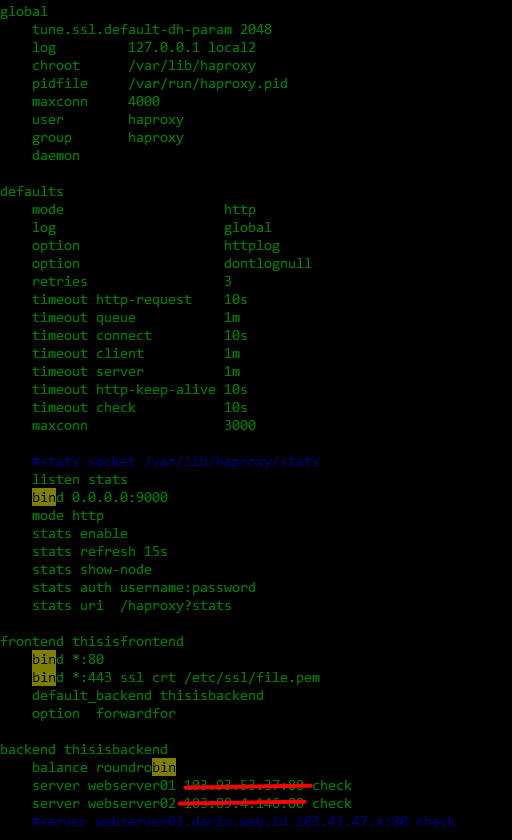
systemctl start haproxy systemctl enable haproxy
Section 3 - Keepalived configuration
LB01 - ssltermination01.darin.web.id as master
cat >> /etc/keepalived/keepalived.conf
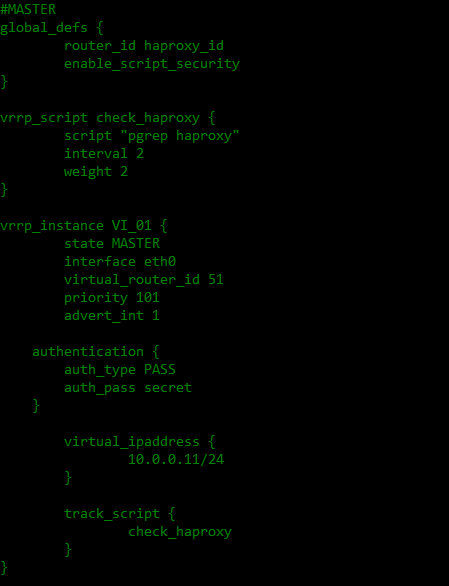
LB02 - ssltermination02.darin.web.id as slave
cat >> /etc/keepalived/keepalived.conf
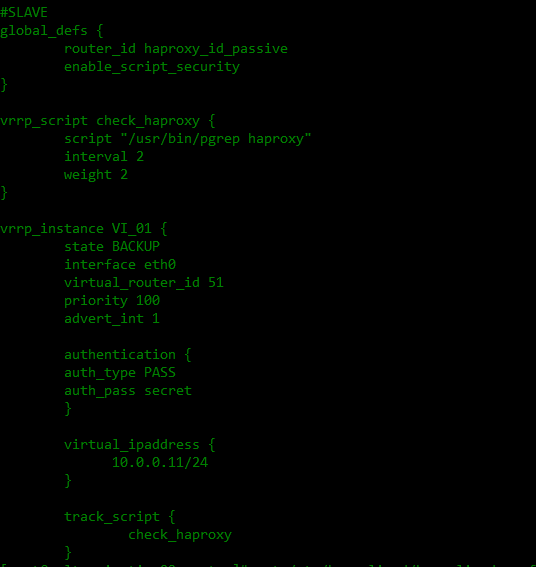
systemctl start keepalived systemctl enable keepalived
Checking result
If haproxy on ssltermination01.darin.web.id up
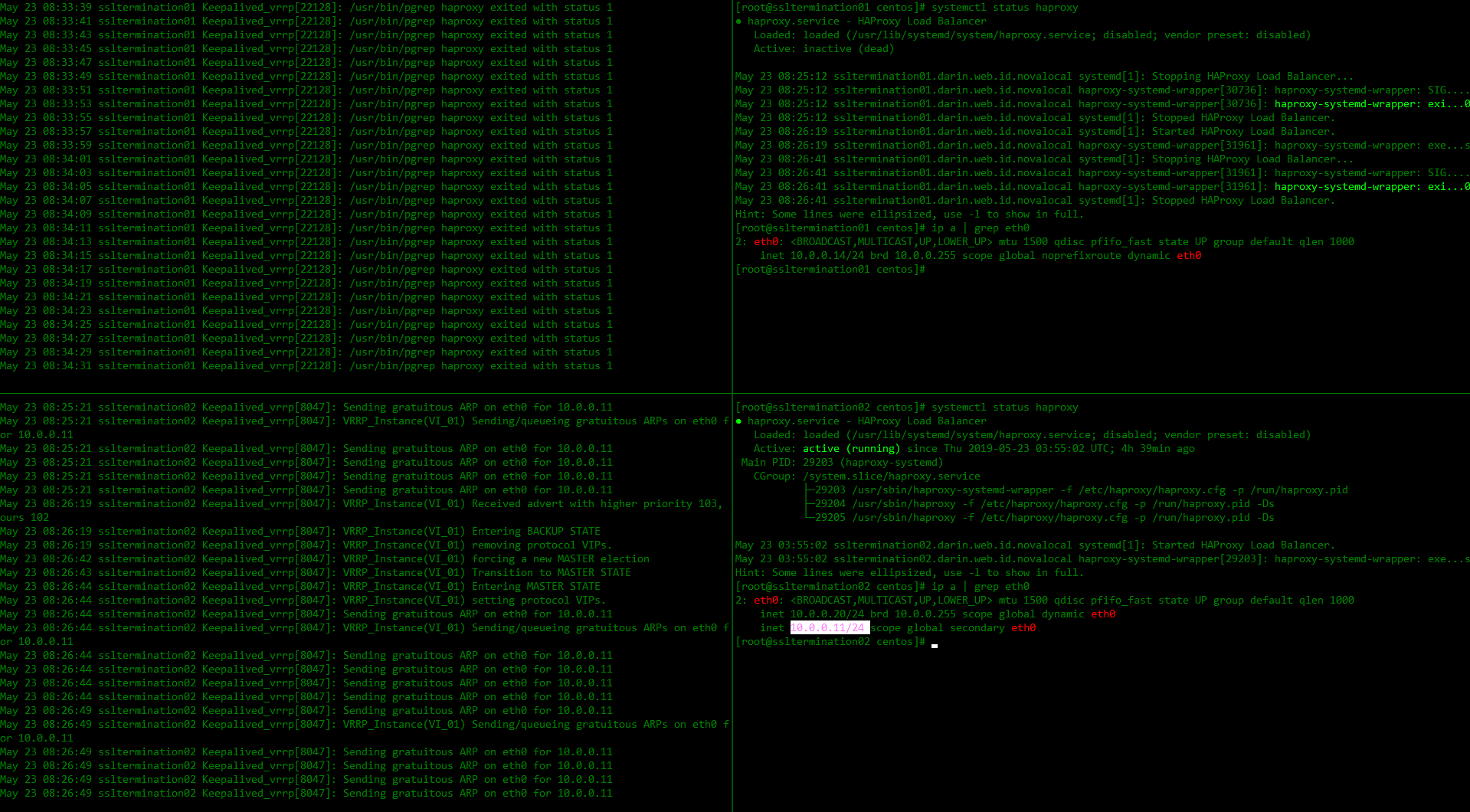
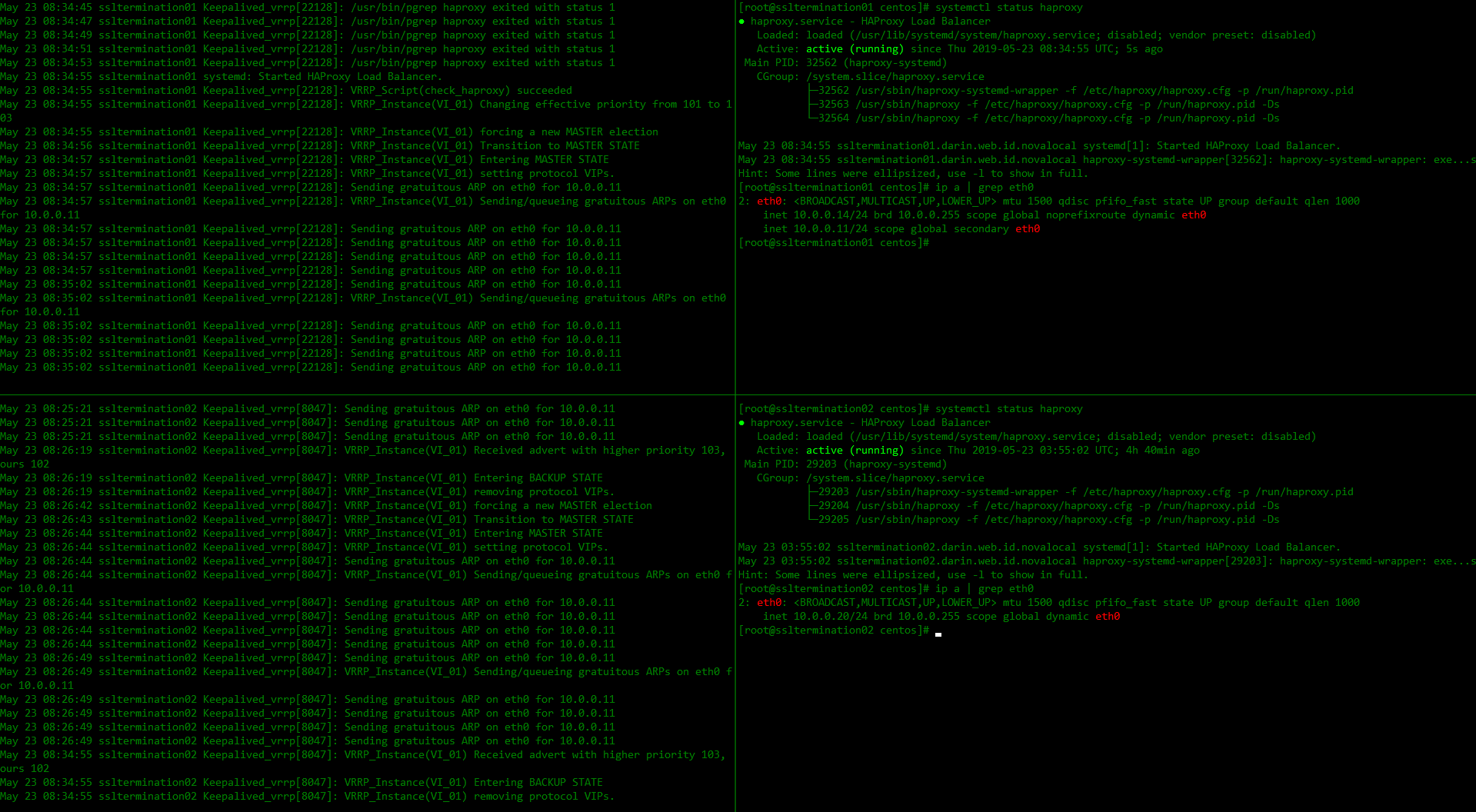 If haproxy on ssltermination01.darin.web.id down
If haproxy on ssltermination01.darin.web.id down
MASTER
global_defs {
router_id haproxy
enable_script_security
}
vrrp_script check_haproxy {
script "/usr/bin/pgrep haproxy"
interval 2
weight 2
}
vrrp_instance V1_01 {
state MASTER
interface ens192
virtual_router_id 51
priority 101
advert_int 1
authentication {
auth_type PASS
auth_pass change-this-password
}
unicast_src_ip 172.18.0.33 #master-local-ip
unicast_peer {
172.18.0.38 #backup-local-ip
}
virtual_ipaddress {
172.18.0.100/24 #desired virtual ip
}
track_script {
check_haproxy
}
}Backup
global_defs {
router_id haproxy
enable_script_security
}
vrrp_script check_haproxy {
script "/usr/bin/pgrep haproxy"
interval 2
weight 2
}
vrrp_instance V1_01 {
state BACKUP
interface ens192
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass change-this-password
}
unicast_src_ip 172.18.0.x
unicast_peer {
172.18.0.x
}
virtual_ipaddress {
172.18.0.100/24
}
track_script {
check_haproxy
}
}
systemctl status keepalived -l