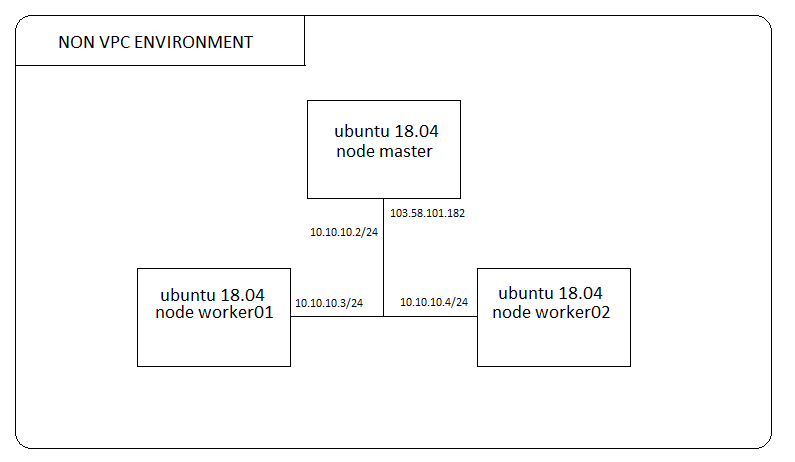
Logical Topology
Requirements https://kubernetes.io/docs/setup/production-environment/tools/kubeadm/install-kubeadm/
Workflow
-
Networking and firewall setup.Execute on each node with root user.
## Mapping node-name in /etc/hosts. cat > /etc/hosts 10.10.10.2 kubernetes.maste 10.10.10.3 kubernetes.worker01 10.10.10.4 kubernetes.worker02 ## Adding user with sudo privilleges. adduser kubernetes passwd kubernetes usermod -a -G sudo kubernetes ## Disabling ufw service. systemctl stop ufw systemctl disable ufw ## Disabling swap support. swapoff -a ## Allowing required ports. Depend on your firewall environment. You need to open port 6443, 2379-2380, 10250-10252 on master node. You need to open port 10250, and 30000-32767 on worker node.
-
Node preparation. Execute on each node with kubernetes user.
## Update and upgrading system. sudo apt update -y; sudo apt upgrade -y; sudo apt autoremove ## Install required packages and docker sudo apt install -y docker.io; sudo docker version sudo apt install -y apt-transport-https; curl -s https://packages.cloud.google.com/apt/doc/apt-key.gpg | sudo apt-key add - ## Adding kubernetes repository. sudo echo "deb http://apt.kubernetes.io/kubernetes-xenial main" > kubernetes.list sudo mv kubernetes.list /etc/apt/sources.list.d/kubernetes.list ## Install kubectl, kubelet, and kubeadm. sudo apt update -y; sudo apt install -y kubectl kubelet kubeadm sudo apt-mark hold kubelet kubeadm kubectl
-
Kubernetes master setup. Execute on master node with kubernetes user.
## Master initialization sudo kubeadm init --pod-network-cidr=10.244.10.0/16 ## Copy configuration mkdir -p $HOME/.kube sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config sudo chown $(id -u):$(id -g) $HOME/.kube/config ## Install POD Network flannel wget https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml kubectl apply -f kube-flannel.yml watch -n1 kubectl get pods --all-namespaces ##wait until all pods state became ready ## Displaying token and token-ca-cert-hash for worker initialization. sudo kubeadm token list sudo openssl x509 -pubkey -in /etc/kubernetes/pki/ca.crt | openssl rsa -pubin -outform der 2>/dev/null | openssl dgst -sha256 -hex | sed 's/^.* //'
- Kubernetes worker setup. Execute on worker node with kubernetes user.
## Join to master sudo kubeadm join --token [TOKEN] [NODE-MASTER]:6443 --discovery-token-ca-cert-hash sha256:[TOKEN-CA-CERT-HASH]
- Kubernetes cluster verification. Execute on maser node with kubernetes user.
kubectl config view kubectl cluster-info kubectl get nodes
-
Kubernetes Dashboard Setup. Execute on master node with kubernetes user.
## Installation kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta4/aio/deploy/recommended.yaml ## Verificition kubectl get svc --all-namespaces -o wide kubectl -n kubernetes-dashboard get svc ## Exposing Kubernetes Dashboard ## Change type: ClusterIP to NodePort. kubectl -n kubernetes-dashboard edit svc kubernetes-dashboard kubectl get svc --all-namespaces -o wide ## Set Permissive RBAC Permission kubectl create clusterrolebinding permissive-binding --clusterrole=cluster-admin --user=admin --user=kubelet --group=system:serviceaccounts ## Accessing Kubernetes Dashboard kubectl get secrets; kubectl describe secrets [secret-name] kubectl --kubeconfig config/admin.conf -n kube-system describe secret $(kubectl --kubeconfig config/admin.conf -n kube-system get secret | grep admin-user | awk '{print $1}')